|
By James L. Morrison and George
Keller
[Note: This is a re-formatted manuscript that was originally published in Planning for Higher Education,
Winter 1992-93, 21, pp. 27-34. It is posted here with permission from the Society for College and University of
Planning (SCUP).]
Nearly all American colleges and universities now realize
that the environment in which they operate has become turbulent and in
some cases threatening. In moving away from excessive attention to their
internal operations and politics toward an alert scrutiny of societal
changes and outside forces—from wish-list planning to strategic
planning—institutions
have been struggling to find an appropriate way to monitor their external
environment.
Numerous methods for doing so through environmental scans
have been tried by colleges and universities over the past 10 years: issues
management schemes (Hearn and Heydinger 1985; Lozier and Chittipedi, 1986;
Murphy 1989), methodical scans (Fahey and Narayanan 1986; Callan 1986;
Morrison 1992; Morrison 1987; Morrison and Mecca 1989; Pritchett 1990),
and
numerous variations in between. While several strategic
trend intelligence systems have produced extraordinary data and enabled
campus administrators and faculty to become more aware of the external
changes likely to affect their lives, environmental scanning as it has
been evolving has some drawbacks.
Environmental scans are time-consuming and can be expensive.
They often do not involve leaders at the university.
And scans usually require many persons to work on them. For example, the
scanning program or the Georgia Center for Continuing Education—one
of the nation's most thorough—uses 65 scanners from four operational
divisions, as well as two committees to review all the
scanning data and to develop policy and suggest changes based on the data.
Cardinal Strich College in Milwaukee, Wisconsin,
employs 80 individuals to scan 199 different publications regularly for
its excellent external events intelligence reports.
Also, broad environmental scans produce some information
on trends only remotely connected to higher education, and information
that may not be useful for specific colleges, given their nature, size,
and location. The result: environmental scans may be weakly linked to
policymaking and strategic institutional changes. Small colleges especially
have difficulty mounting a sophisticated. comprehensive environmental
scan. Finally, the financial difficulties at many institutions during
the 1990s have inhibited campuses from making new investments of staff
time and money to monitor the host of external changes in society.
New technique on the block
Both of us, therefore, have separately been experimenting
with and developing a form of environmental probe that is less
time-consuming, less labor intensive, and less expensive. One that is more institution-specific
and more likely to result in swift decisions and constructive changes.
And one that involves busy faculty and campus leaders themselves.
We think we have developed an instrument that fits most
of these criteria. We call it the institutional vulnerability audit.
It derives in part from a little-known procedure proposed
in 1977 by SRI International and called by them a "vulnerability
analysis." What these California researchers suggested was that companies
constantly should assess those customer bases, cost structures, technologies,
competitive conditions, political climates, and social values they regard
as critical to their success, and carefully watch the environmental changes
that would undermine those critical elements, leaving the companies vulnerable
to disruption and decline (SRI 1977). The key question is: "What
supporting elements in the environment, if diminished or taken away, might
impair or seriously weaken the organization?"
Thus, for example, a college devoted to teaching engineering,
technology, and science might be radically affected if nearly everyone
was suddenly able to have a personal computer, or if secondary school
students began taking fewer mathematics and science
courses, or if the tax laws changed to discourage corporate giving to
universities. This is what happened to some extent to Lehigh University
in Pennsylvania, which has been traditionally heavy in training scientists,
engineers, and technicians, but in the past decade has become increasingly
filled with students who want to major in business. Similarly, in recent
decades many women's colleges have been forced to become coeducational
because of changing gender values and attitudes (Pampusch 1991). And
changing demographics. Erosion in the high schools, and inner-city changes
have made the traditional purposes of numerous community colleges vulnerable
(Eaton 1992).
The institutional vulnerability audit is a way of scanning
only those portions of society's changes that directly impinge on the
central features of an individual college or university. It puts boundaries
on the environmental scan. The audit requires an institution to ask itself
what underpinnings are necessary for its continued successful operation,
and examines those underpinnings in detail to see how they are changing
and how the changes could affect the institution.
Most colleges and universities in trouble today have assumed
the continuation of past trends and practices and have neglected discontinuities
and subtle shifts. They failed to identify the potentially threatening
forces that could wound them. Often they over-looked potentially damaging
changes because their dominant concern in planning was with growth, add-ons,
new dollars, novel programs. But the first rule of any institution is
survival, and this mandates a fierce defense of established domain. The
primary planning obligation of the 1990s, a decade of discontinuities,
is avoidance of serious vulnerabilities. Growth in quality and innovation
continue to be imperative, of course, but both can be built only on a
reasonably stable foundation.
Looking vulnerability in the eye
We think the vulnerability audit should be conducted at
least biennially, though some colleges in especially protean settings
may prefer to conduct the audit annually, as they do with their financial
audit. We think it should be carried out by a relatively small team—to 10 persons at smaller colleges and 10 to 15 at large
universities—comprised
of senior leaders and outstanding faculty representing major functional
areas of the institution. It is important that senior administrators and
faculty conduct the audit so that it benefits from the best thinking,
so that the environmental scan can be directly comprehended by the
decision-makers,
and so that results of the audit can lead quickly to operational changes
or strategic new initiatives.
The vulnerability audit consists of five steps, which
are transparently logical in their sequence.
The first step is to identify the environmental
footings of the college or university. The underpinnings can be tangible,
as in a steady, pool of incoming traditional students from three or four
states, or a high percentage of alumni contributors as at Kentucky's Centre
College, Williams College, and Dartmouth, or an increasing sum of money
each year from the state's legislators and governor, as Arizona State
experienced until last year. The underpinnings can also be intangible,
as in the public's sense of the worth of giving money to colleges and
universities or the attitude of black students about attending predominantly
white colleges.
It is probably necessary to devote at least a half day
to step one. Begin with the nominal group technique by asking each member
of the team to offer his or her own candidates for the vital underpinnings
for the college. On what is the college dependent for its continued stability? After each person has separately contributed, switch to the group brainstorming
technique to solicit from the team collectively any underpinning that
may have been overlooked during their individual donations of views. The
point is to identify as many crucial areas as possible for the successful
operation of the college or university.
The second step is to identify the forces, shifts,
trends, and events that could damage the institution's health and quality.
What developments in society could undermine each of the dependencies
or underpinnings identified in step one? For example, one highly academic
and noted liberal arts college which has styled itself as progressive
and welcoming to people of alternative lifestyles and strong political
passions currently finds itself vulnerable in admissions because more
of today's outstanding applicants are conservative, prefer economics,
science, computer studies, and professional studies, and eschew the counterculture
and "granola'' liberals. This second stage requires a great deal
of imagination, and members should be encouraged to be bold and creative.
(Schwartz 1991). It is useful to post each of the vital underpinnings from
step one on an easel sheet, and then list underneath the new conditions
that could damage each of them.
Ignore the probabilities of the imagined changes happening
at this point. Reach out beyond the conventional, even though some projected
happenings may seem bizarre. (The dissolution of the Soviet Union, the
recent increase of illiteracy in the United States, and the strength of
the current attacks on higher education may have
seemed bizarre five years ago.)
In step three, switch to the Delphi process. a
forecasting technique where leading experts present oracular predictions
of the likelihood and probable impact of new developments in some field
(Salancik, Wenger, and Helfer 1971). In a campus IVA the experts are the
team members. The team should number each of the threats of the college's
underpinnings. It is helpful at this stage to hand out a chart like that
depicted in Figure 1 to each member. After numbering each of the
perceived threats to the college's underpinnings, ask team members to
evaluate independently the probability of each threat on one axis and
its likely impact on the institution on the other axis, then record the
position of each threat by a number on the chart.
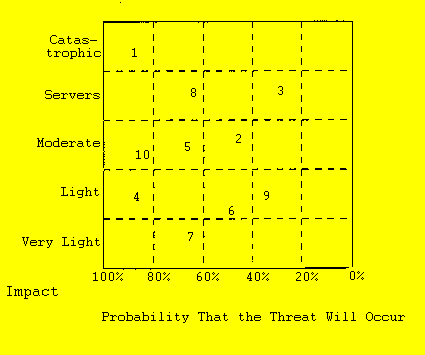
Figure 1: One individual's probability/impact chart
showing an assessment of 10 threats.
Each threat to the underpinnings should be stared in terms
of an event or condition that could occur within a specified time. (Examples:
Within five years federal overhead rates for research could drop to a
maximum of 50 percent, or within three years two-thirds of all freshmen
will require remedial mathematics and introductory statistics.) Have each
member mark his or her chart with a number for his or her assessment of
the probability and impact of the threat.
Then, in the second part of step three, pool the individual
evaluations for each of the perceived threats on master charts—one
for each threat, as shown in Figure 2. This can be done on a chalkboard
or easel pad. These charts will display the degree of consensus of each
threat. If there are deviant or outlying appraisals, ask the members who
offered them to express their reasoning for the evaluations. Sometimes
these articulated reasons will cause some other ream members to reassess
their position.
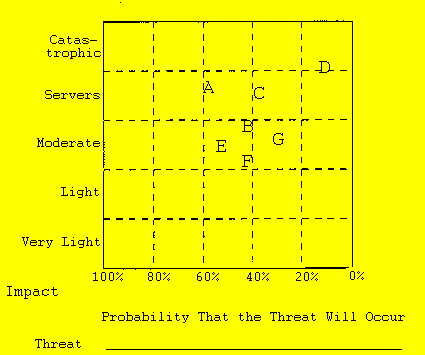
Figure2: Team's probability/impact threat
assessment chart showing its assessment of one threat.
Still going
You are now ready for step four: a review of the
overall pattern of threats to the institution and the degree of its vulnerability.
Begin with a thorough discussion of each of the external threats to the
university. Then, with the aid of the vulnerability chart, as in Figure
3, The team should rate each of the threats for likely impact
and probability of happening.
Threats in quadrant 1 will be those to which the college
is most vulnerable. These possibilities demand immediate attention, with
prompt and powerful strategies to ward off the threats and to reduce their
impact, and contingency plans in case they occur very soon.
The threats in quadrant II are likely to be the real "sleepers,"
and will require careful study and monitoring. You will find that the
vulnerability audit team usually reaches a much greater consensus about
the impact of outside developments than about the probability of
occurrence. This is because campus leaders know more about their institution
than they know about the external environment. There is a chance, therefore,
that the probabilities of upsetting events happening are being rated too
low.
The team may wish to consult outside experts or several
scholars on the faculty who are highly knowledgeable about specific areas,
such as threats from new developments in communications technology or
your state's politics. Or they may wish to have the institutional research
or a research librarian gather more information about these areas to enable
more informed judgments.
The moderate threats in quadrant III can often be addressed
by taking thoughtful preventive action. For example, if the team estimates
that the maintenance workers or security guards might go out on strike
or demand out-of-line wages, the institution should probably identify
a labor mediator or begin looking at the costs of outside maintenance
and security services and of temporaries. Or if the college is admitting
Hispanic students at a brisk pace but not appointing new Hispanic faculty,
the institution might launch an intensive effort
to identify young Hispanic scholars to recruit, or establish a new fellowship
program to attract outstanding Hispanic graduate or post-doctoral students
who could be used as instructors and become faculty members.
Quadrant IV threats usually consist of annoyances—power
outages, an unusually cold winter, the resignation or sudden death of
a very popular dean, teacher, or athletic coach, the relocation of a major
local industry, a new newspaper editor who dislikes your institution or
intellectuals, or a demand by the local government for a tax contribution
for the municipal or county fire department. Contingency plans can usually
handle such possible changes.
In the fifth and final step the team should design
strategies to overcome, subdue, or lessen each of the vulnerabilities,
assign persons to be responsible for directing each strategy, and allot
resources to carry out the priority actions.
Limitations and benefits
The institutional vulnerability audit is not without its
limitations. The process does not address the problems caused largely
by internal factors, nor does it include a competitor analysis. Unlike
the now-standard SWOT analysis—strengths, weaknesses, opportunities,
and threats—it concentrates on the threats. Also, the two-day retreat
for the vulnerability audit may be insufficient time. The process depends
on shrewd and insightful contributions by senior campus experts, who may
not attuned to examining the effects of social and economic changes on
campus operations.
But the vulnerability audit draws on the expertise and
experienced judgment of the institution's leaders and compels them to
acknowledge outside threats and construct defenses to keep the institution
stable. By identifying environmental threats early, leaders have time
to monitor them, to review options, and to plan for changes to diminish
the emerging threats. With a vulnerability audit, a college can better
avoid unpleasant surprises. It provides an early warning system that can
help protect the institution's academic and fiscal integrity.
There are other benefits. The vulnerability audit can
help improve communication among departments and divisions, and it links
senior administrators and faculty in devising strategies and fosters collaborative
management. Also, the vulnerability audit is relatively inexpensive and
is frugal with that scarcest of resources among busy executives and scholars:
time.
Most important, perhaps, the vulnerability audit does
not waste resources, but ties environmental scanning and monitoring directly
to the future of your own institution. The search is not wide-ranging
and vagrant but pointed and highly relevant. The focus is squarely on
those environmental trends, events, and conditions that may cause the
biggest problems for your own institution. Also, by having senior leaders
engage in the process the distance between external threats and strategic
actions to prevent difficulties is reduced.
Above all, the institutional vulnerability audit helps
campuses to know themselves, and to know what ingredients are vital in
keeping the institution strong. Knowing where a college is vulnerable
helps focus time, money, and care on those people, activities, and conditions
that provide indispensable support for the college or university.
The better institutions will always be opportunity seekers
as well as protectors of their flanks. But no army should plan major new
activities unless its supply routes are secure. In the 1990s. when higher
education faces diminishing financial support,
declining
public trust, and an eroding base of traditional students, strategic planning
should concentrate first on the changes that reduce vulnerability. The
IVA is a new tool to do just that.
References
Bourgeois, L 1980. Strategy and Environment: A Conceptual
Integration. Academy of Management Review 5: 25-39.
Callan, P. ed. 1986. Scanning for Strategic Leadership.
New Directions in Institutional Research, no. 52. Jossey-Bass.
Cameron, K 1983. Strategic Responses to Conditions of
Decline. Journal of Higher Education 54: 359- 380.
Eaton, J. 192. The Coming Transformation of Community
Colleges. Planning for Higher Education 21(1): 1.
Fahey, L and V. Narayanan. 1985. Macroenvironmental
Analysis for Strategic Management. West Publishing Company.
Friend, J. and A. Hickling. 1987. Planning Under Pressure:
The Strategic Choice Approach. Pergamon Press.
Hearn, J. and R Heydinger. 1985. Scanning the University's
External Environment. Journal of Higher Education. 56: 419-445.
Keller, G.1983. Academic Strategy. Johns Hopkins
University Press.
Lozier, G. and K Chittpedi. 1986. Issues Management in
Strategic Planning. Research in Higher Education 24:
3-13.
Marien, M. 1991. Scanning An Imperfect Activity in an
Era of Fragmentation. Futures Research Quarterly 7: 82-90.
Mecca, T. and J. Morrison, 1988. Pathways to the Future:
Linking Environmental Scanning to Strategic Management.
Community College Review. 15: 34-44.
Miliken, F.1987. Three Types of Perceived Uncertainty
About the Environment. Academy of Management Journal
12: 133-143.
Morrison, J.1992. Environmental Scanning. In A Primer
for New Insitutional Researchers. eds. M. Whitely, J. Porter, and
R. Fenske. Association for Institutional Research.
Morrison, J. and T. Mecca. 1989. Managing Uncertainties:
Environmental Analysis/Forecasting in Academic Planning. In Higher
Education: Handbook of Theory and Research. ed. J. Smart (5: 351-382).
Agathon Press.
Murphy, J. 1989. Identifying Strategic Issues. Long-Range
Planning 22: 121-125.
Pampusch, A. l991. What Strategy for Women's Colleges?
Planning for Higher Education 20(1): 24-28.
Pritchett, M. 1990. Environmental Scanning in Support
of Planning and Decisionmaking. Paper presented at the annual meeting
of the Association for Institutional Research, Louisville. Kentucky.
Salancik, J., W. Wenger, and E. Helfer. 1971. The Construction
of Delphi Event Statements. Technological Forecasting and Social Change
3: 65-73.
Schwartz, P. 1991. The Art of the Long View. Doubleday
Currency.
SRI. 1977. Vulnerability Analysis: What lt ls and What
it Does. In SRI Business Intelligence Program Report No.593. SRI International.
Whiteley, M., J. Porter, and J. Morrison. 1990. Developing
Scenarios: Linking Environmental Scanning and Strategic Planning. Planning
for Higher Education 18(4): 47- 60.
|



